Lynis是针对Unix/Linux的安全检查工具,可以发现潜在的安全威胁。这个工具覆盖可疑文件监测、漏洞、恶意程序扫描、配置错误等。
检查项举例:
系统允许的登陆操作 失效的SSL证书 不需要密码的账户 未授权的文件 配置错误
Lynis是针对Unix/Linux的安全检查工具,可以发现潜在的安全威胁。这个工具覆盖可疑文件监测、漏洞、恶意程序扫描、配置错误等。
检查项举例:
系统允许的登陆操作 失效的SSL证书 不需要密码的账户 未授权的文件 配置错误
It’s great that Microsoft has made Windows 8.1 entirely free to owners of Windows 8, but unfortunately you’re limited to installing the update through the Windows Store — unless you’re an MSDN subscriber there’s no ISO you can grab to install the operating system how and when you like.
But as enterprising Reddit user redditorfor0seconds has discovered, there is a way of getting your hands on the ISO that only requires you to have a Windows 8 retail or MSDN key (but not an OEM key, apparently). It’s incredibly straightforward too, just follow these simple instructions:
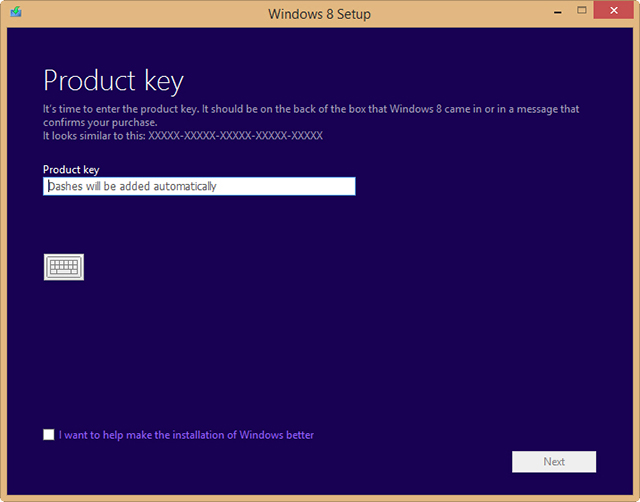
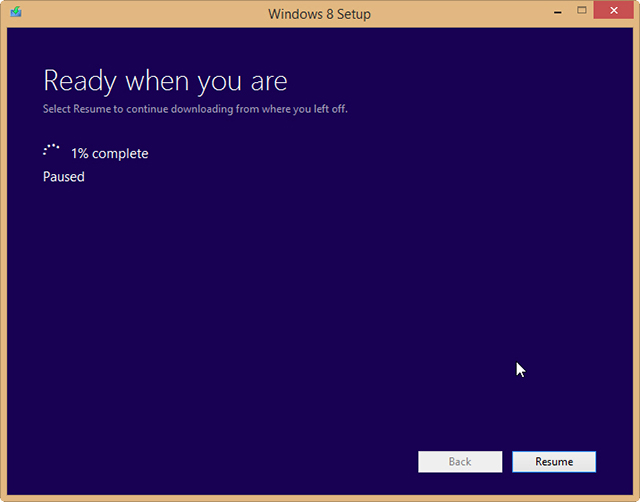
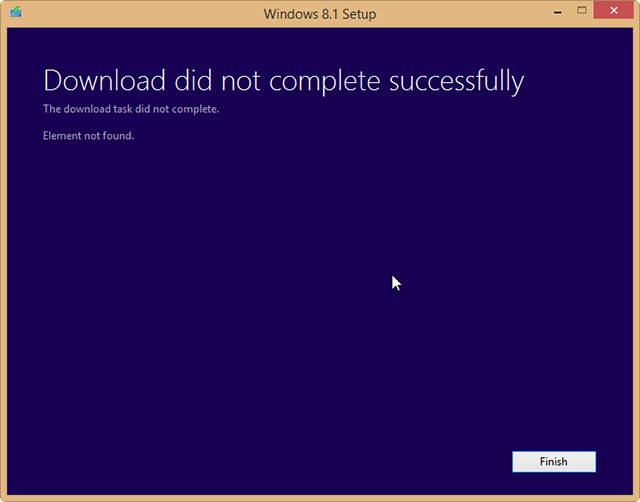
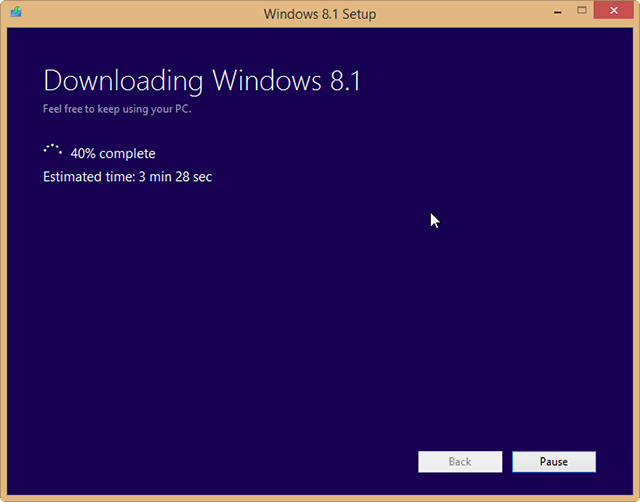
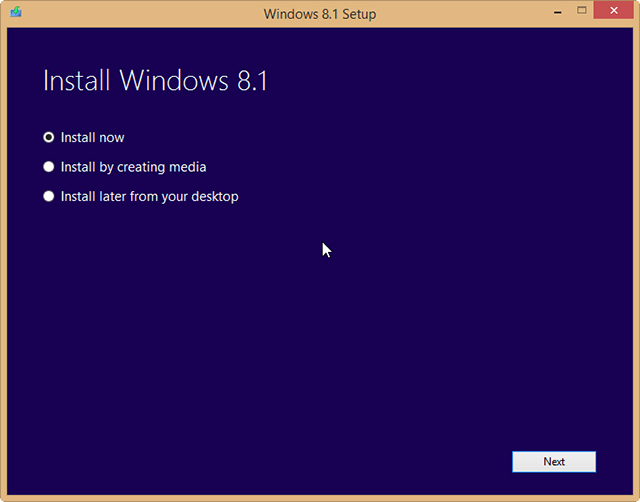
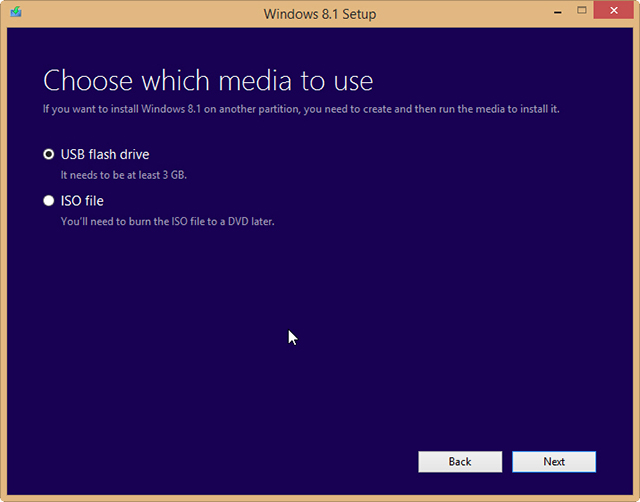
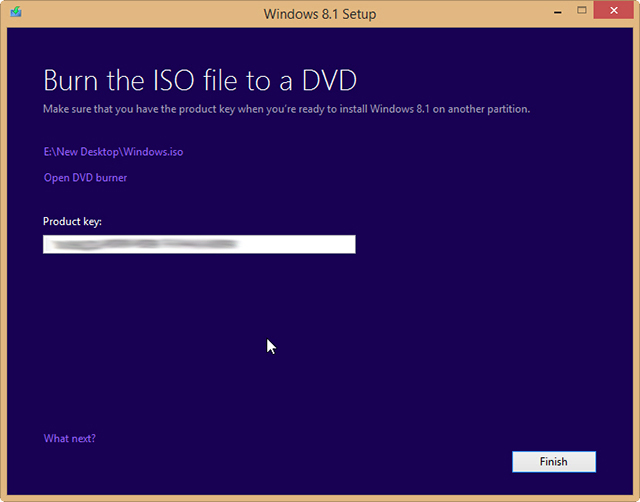
The method worked perfectly for me, but your mileage may vary. If you try it let me know how you get on in the comments below.
There is a good chance you read your mail from Gmail with Mac’s native Mail app. There is also a good chance you never really paid attention to how much disk space all this content synced with Gmail IMAP really takes up. Having recently replaced my internal 160 GB hard drive with an Intel X25-M SSD drive half the size, I’m naturally eager to strip all the unnecessary stuff out of the system in order to save some SSD space. So how to free a few gigabytes of space from Gmail?
This question has long been lingering around, it’s just that I didn’t care about it when I still had disk space to throw away: Why does ~/Library/Mail/IMAP-marknanut[…] folder take up almost triple the size (some 7 GB) of the amount of actual mail being shown in my Gmail web account (some 2.5 GB)? Gmail messages seem to take up too much space when used with Mail.app (or any other client that uses IMAP, really). Right click on the “IMAP-youraccountname” folder and select Get Info to see its size:
Ok, this isn’t that hard to find out and goes roughly like this: Gmail’s tags are not exactly compatible with IMAP’s folder logic, thus being displayed as folders in IMAP. In very rough terms: a mail with multiple tags, say 2 or 3 tags, gets locally copied to the same number of folders with these tag names (2 or 3 folders). If you do a Spotlight search in Mail, you’ll usually get duplicate results – for instance the same received mail message appears in “All Mail”, “Inbox”, also “Starred” and so on, whereas a sent message appears in “Sent Mail” and “Sent”.
It would obviously be best to prevent Mail.app from downloading folders where there are most certainly mail duplicates. You’ll figure it best for yourself, but for a start we can eliminate the “All Mail” folder. So how to do it?
Inspired by the post of Rajiv Pant, I went to my Gmail settings, and under Labs section I enabled “Advanced IMAP controls”.
Next uncheck all tags (folder) you don’t want to download locally (for instance “All Mail”) in the Labels section.
I also unchecked “Starred” and “Spam”. I restarted Mail.app, and voila – no All Mail, Starred and Spam folders, no duplicates and more than 4 GB extra space.
Which IMAP folders you’ll prevent from downloading, is of course up to you to figure out. I wish you success. Check out Rajiv Pant’s post too. ![]()
【转载本文不写出处的,男的木丁丁,女的满脸都是丁丁】
出自http://chichou.0ginr.com/blog/328
昨晚上偶然看到个比较坑爹的日志,正文有一张图片,在好友动态列表查看的时候可以显示自己(不是发日志的好友,是你自己)的头像和QQ号码、昵称。正文的文字称,这是“本年度最给力神奇魔力日志(转载会看到你最熟悉的身影)”,并且在文章底部附加了一个发广告的QQ号码。
由于这张坑爹图片的存在,文章转发量短短三天内过千。这招可比那些疯狂加群发广告的来的更有创意和杀伤力,转载传播图片(包括日志当中的广告)的人几乎是全网用户(跟所谓病毒营销差不多了)。好奇的话可以看这篇日志最初来源:hXXp://user.qzone.qq.com/732678621/blog/1363502247
一看就知道是检测referer的把戏。早在几年前BBS还在流行的时候,很多人设置的签名图具有天气预报、客户端信息(浏览器、操作系统、IP所在地之类)、随机笑话、倒计时等五花八门的功能。这都得益于服务器端脚本的图像处理功能。而客户端的检测则是基于HTTP请求中的UserAgent和Referer等信息。
但是印象中QQ空间为了防止referer潜在的安全问题和防止图片被防盗链下了很大功夫,凡是发表到QQ空间的日志,正文都会把引用到的所有第三方图片资源缓存到腾讯的云端上。所以直接在日志正文中引用的图片,是不会提交REFER到我们的服务器脚本上的。
更新:有人发现只要响应HTTP请求的时候输出状态200,但不输出任何内容,腾讯就不会缓存这张图。
文中特别称,“请转载后用电脑进入个人中心看”。为什么要特别说明是“个人中心”呢?我刷新了好久的动态,终于看到了图片所说的效果。页面生成的DOM代码为:
|
1
2
3
|
onload="QZFL.media.reduceImage(0,400,300,{trueSrc:'http:\/\/qq.sennvwu.com\/qzone\/do.php',callback:function(img,type,ew,eh,o){var _h = Math.floor(o.oh/o.k),_w = Math.floor(o.ow/o.k);if(_w<=ew && _h>=eh){var p=img.parentNode;p.style.width=_w+'px';p.style.height=_h+'px';}}})" width="400"> |
原来QQ空间还是会显示源地址的图片的,仅限于在“个人中心”。这时候请求图片附带的HTTP_REFERER的值为
http://user.qzone.qq.com/123456789/infocenter
号码就是这样提取到的。如果REFERER不满足条件,这个php将在header中发送Location跳转到同一目录下的no.png。
那么后台是如何取到QQ头像、昵称等信息的呢?我Google到了一个腾讯的WebService接口:
http://base.qzone.qq.com/fcg-bin/cgi_get_portrait.fcg?uins=123456789
不需要任何凭证信息即可获取uins指定的QQ号码的头像、昵称信息,返回的格式为JSON。另外上面的图片还有一个显示地理位置和ISP的功能,这个就比较常见了。我找到了一个比较好用的接口,来自TB:
格式同样也是JSON。
接下来实现这个效果就比较简单了,通过REFERER检测用户的QQ号码,然后在后台下载头像、昵称等信息,用GD函数绘制上图片,返回客户端。
我也折腾了一个‘神奇图片“发到空间,居然捉弄了一群人。下面是php语言的实现代码。为了减少后端的流量,对下载的头像做了缓存处理:
|
001
002
003
004
005
006
007
008
009
010
011
012
013
014
015
016
017
018
019
020
021
022
023
024
025
026
027
028
029
030
031
032
033
034
035
036
037
038
039
040
041
042
043
044
045
046
047
048
049
050
051
052
053
054
055
056
057
058
059
060
061
062
063
064
065
066
067
068
069
070
071
072
073
074
075
076
077
078
079
080
081
082
083
084
085
086
087
088
089
090
091
092
093
094
095
096
097
098
099
100
101
102
103
104
105
106
107
108
|
error_reporting(0);ob_start();header('Content-Type: image/png');define('IMG_NO', "no.png"); #刚开始显示的提示信息define('IMG_BACKGROUND', "background.png");define('IMG_WIDTH', 400);define('IMG_HEIGHT', 128);define('FONT_NAME', "AdobeHeitiStd-Regular.otf"); #字体文件名define('CACHE_PATH', rtrim(realpath("./cache"), '/').'/'); #缓存目录define('CACHE_EXPIRE', 60*60); #缓存时间,单位秒#(!is_dir(CACHE_PATH) && is_writable(CACHE_PATH)) || die;/* $remote: 远程URL $local: 本地缓存路径 $expire: 过期时间。为-1时,永久不更新缓存*/function load_from_cache($remote, $local, $expire = CACHE_EXPIRE, $as_path = false) { //过滤潜在的危险字符 $local = preg_replace("/[.\/\\\?\*\'\"\|\:\<\>]/", "_", $local); $cache = CACHE_PATH.$local; //查找缓存 if(file_exists($cache) && ($expire = -1 || filemtime($cache) - time() < $expire)) return $as_path ? $cache : file_get_contents($cache); //文件不存在或缓存过期,重新下载 $content = file_get_contents($remote); file_put_contents($cache, $content); return $as_path ? $cache : $content;}/* 返回客户端信息。*/function client_info() { $ip = ($_SERVER["HTTP_VIA"] && $_SERVER["HTTP_X_FORWARDED_FOR"] ? $_SERVER["HTTP_X_FORWARDED_FOR"] : $_SERVER["REMOTE_ADDR"]); $info = explode('"', load_from_cache($url.$ip, $ip, -1)); $string = $info[7].$info[23].$info[31].$info[47]; return json_decode('"'.$string.'"');}$referer = $_SERVER['HTTP_REFERER'];//$referer = "http://user.qzone.qq.com/123456789/infocenter";$pattern = "/http:\/\/user.qzone.qq.com\/(\d+)\/infocenter/";if(preg_match($pattern, $referer, $matches)) { //获取QQ号码 $uin = $matches[1]; $info = explode('"', load_from_cache( $avatar = $info[3]; $nickname = iconv("GBK", "UTF-8//IGNORE", $info[5]); $client = client_info();//重点来了,生成图片 try{ $im = imagecreatefrompng(IMG_BACKGROUND);//绘制头像 $avatar_file = load_from_cache($avatar, $uin.".jpg", 60*60*24, true); $im_avatar = imagecreatefromjpeg($avatar_file); imagecopymerge($im, $im_avatar, 14, 14, 0, 0, 100, 100, 100); imagedestroy($im_avatar);//绘制文字 $blue = imagecolorallocate($im, 0, 0x99, 0xFF);$white = imagecolorallocate($im, 0xFF, 0xFF, 0xFF);$texts = array( array(12, 148, 40, $white, $uin), array(18, 125, 70, $blue, $nickname), array(16, 125, 100, $blue, $client) );foreach($texts as $key=>$value) { imagettftext($im, $value[0], 0, $value[1], $value[2], $value[3], FONT_NAME, mb_convert_encoding($value[4], "html-entities", "utf-8")); //解决乱码问题 }imagepng($im); imagedestroy($im);header("Content-Length: ".ob_get_length()); ob_end_flush(); } catch (Exception $e) {//die($e->getMessage()); $error = true; }} else { $error = true;}//更新:在这里直接停止输出即可防止图片被缓存die();/*if($error){ header('Content-Length: '.filesize(IMG_NO)); echo file_get_contents(IMG_NO);}*/ |
WORDPRESS把缩进都吞掉了,看上去非常不爽。下面还是直接给出我的打包吧,连图片也有。不过字体文件太大而且有版权纠纷,请自行准备。
开启Binary log(二进制日志)记录Mysql更新内容,在服务重启或者超出binlog大小上限的情况下mysqld会创建新的binlog,时间长了本地会保留很多binlog,我们应将历史binlog清除
1.刷新日志
mysql > flush logs;
2.查看当然数据库binlog信息
mysql > show binary logs;
+——————+———–+
| Log_name | File_size |
+——————+———–+
| mysql-bin.000023 | 149 |
| mysql-bin.000024 | 149 |
| mysql-bin.000025 | 149 |
| mysql-bin.000026 | 149 |
| mysql-bin.000027 | 149 |
| mysql-bin.000028 | 106 |
+——————+———–+
3.清除历史log,保留最近的
mysql > purge binary logs to ‘mysql-bin.000028’;
4.查看binlog事件
mysql > show binlog events;
+——————+—–+————-+———–+————-+—————————————+
| Log_name | Pos | Event_type | Server_id | End_log_pos | Info |
+——————+—–+————-+———–+————-+—————————————+
| mysql-bin.000023 | 4 | Format_desc | 1 | 106 | Server ver: 5.1.31-log, Binlog ver: 4 |
| mysql-bin.000023 | 106 | Rotate | 1 | 149 | mysql-bin.000024;pos=4 |
+——————+—–+————-+———–+————-+—————————————+
5.查看本地binlog文件
# ls -l /data/dbfile
mysql-bin.000028
mysql-bin.index
查看当前使用的Binary log名称
# more mysql-bin.index
./mysql-bin.000023
./mysql-bin.000024
./mysql-bin.000025
./mysql-bin.000026
./mysql-bin.000027
./mysql-bin.000028
备份中清除日志
# mysqldump –flush-logs –delete-master-logs