http://danielgibbs.co.uk/scripts/csgoserver/
About csgoserver
csgoserver is a command line tool for quick, simple deployment and management of a Counter Strike: Global Offensive Linux dedicated server.
Current Version: 251213
Main features
- Server installer (SteamCMD)
- Start/Stop/Restart server
- Server updater (SteamCMD)
- Server monitor (including email notification)
- Server backup
- Server console
Compatibility
The Linux Server Manager is tested to work on the following Linux systems.
- Debian based distros (Ubuntu, Mint etc.)
- Redhat based distros (CentOS, Fedora etc.)
The scripts are written in BASH and Python and would probably work with other distros.
Installation
The installer will automatically download and configure a Counter Strike: Global Offensive server.
Prerequisites
Before installing, please ensure you have all the dependencies required to run the script.
Ubuntu
Ubuntu 32-bit
apt-get install gdb mailutils postfix
Ubuntu 64-bit
apt-get install gdb mailutils postfix lib32gcc1
Debian
Debian 32-bit
apt-get install gdb mailutils postfix tmux ca-certificates
Debian 64-bit
dpkg --add-architecture i386
apt-get update
apt-get install gdb mailutils postfix tmux ca-certificates lib32gcc1
RHEL 6/CentOS 6
Note: EPEL repository or equivalent is required.
http://fedoraproject.org/wiki/EPEL
RHEL 6/CentOS 6 32-bit
yum install gdb mailx wget nano tmux
RHEL 6/CentOS 6 64-bit
yum install gdb mailx wget nano tmux glibc.i686 libstdc++.i686
Install
1. Create a user and login
adduser csgoserver
passwd csgoserver
su - csgoserver
2. Download the script
wget https://raw.github.com/dgibbs64/linuxgameservers/master/CounterStrikeGlobalOffensive/csgoserver
3. Make it executable
chmod +x csgoserver
4. Run the installer and follow the instructions
./csgoserver install
Usage
Running the server
Start the server
./csgoserver start
Stop the server
./csgoserver stop
Restart the server
./csgoserver restart
Updating the server
The server can be updated automatically using SteamCMD. The update option will stop the server, run the SteamCMD update and start the server again.
./csgoserver update
Monitoring the server
The script can monitor the server to ensure it is online. Should the server go offline, the monitor will attempt to start it again.
./csgoserver monitor
Note: see Automation on how to get monitor to run automatically.
Game Server Query Plugin
The Game Server Query plugin adds improved monitoring over the standard monitoring feature.
gsquery.py query’s the server to see if it responds with its server details. If it fails to respond the server will be restarted.
This is particularly useful for if a server has locked or frozen but the server instance/process is still running.
Install Game Server Query Plugin
Download gsquery.py to the same directory as the main script.
wget https://raw.github.com/dgibbs64/linuxgameservers/master/GameServerQuery/gsquery.py
Make it executable
chmod +x gsquery.py
To test is works run monitor and it will state that gsquery.py was detected.
Email notification
Monitoring can send you an email, should the server go offline, and report details of the issue. See example email below:
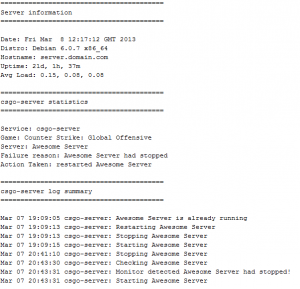
Enable email notification
nano csgoserver
# Notification Email
# (on|off)
emailnotification="on"
email="email@example.com"
Test email notification
You can test email notifications are working without restarting the server.
./csgoserver email-test
Debug mode
Use debug mode to help you if you are having issues with the server. Debug allows you to see the output of the server directly to your terminal allowing you to diagnose any problems the server might be having.
./csgoserver debug
Server Details
If you need to get all main server details you can use the following command.
You will be given the following details if applicable to your server:
- Server Name
- Server Ports
- Rcon Password
- WebAdmin Username
- WebAdmin Password
This can be very useful if you have forgotten your servers details.
./cgsoserver details
Console mode
Console allows you to view the live console of a server as it is running and allow you to enter commands to it.
./csgoserver console
To exit the console press “CTRL+b d”
Note: pressing “CTRL+c” will terminate the server
Backup
Backup will allow you to create a complete gzip archive of the whole server.
This is designed to allow you to backup before making changes to the server just in case there is a problem.
Note: this is not designed to be an automated backup solution
./csgoserver backup
Automation
You can use cronjobs to automate the process of updating and monitoring the server. You can either run the cronjob as root or as the csgoserver user.
Server update
Update the server at 5am daily.
Root Cronjob
crontab -e
0 5 * * * su – csgoserver -c ‘/home/csgoserver/csgoserver update’ > /dev/null 2>&1
csgoserver Cronjob
crontab -e
0 5 * * * /home/csgoserver/csgoserver update > /dev/null 2>&1
Server Monitor
Check every 5 mins is the server is online.
Root Cronjob
crontab -e
*/5 * * * * su - csgoserver -c '/home/csgoserver/csgoserver monitor' > /dev/null 2>&1
csgoserver Cronjob
crontab -e
*/5 * * * * /home/csgoserver/csgoserver monitor > /dev/null 2>&1
Configuration
Start parameters
If you need to adjust the start parameters you can edit the ‘parms’ variable under ‘Start vars’ in the script.
parms="-game csgo -console -usercon +game_type 0 +game_mode 0 +mapgroup mg_bomb +map ${defaultmap}"
See this link for all available start parameters.
https://developer.valvesoftware.com/wiki/Command_Line_Options#Source_Dedicated_Server
Config File
The server has a default config file that will allow you to edit many different settings.
To find the config file use the details command.
./csgoserver details
Default ports
Gameport (Inbound): 27015 UDP
Source TV (Inbound): 27020 UDP
Client Port (Outbound): 27005 UDP
Should you need to change the port edit the start variables and amend the port to meet your requirements.
port="27015"
sourcetvport="27020"
clientport="27005"
Multiple Servers
It is possible to run multiple server instances.
I recommend repeating the installation however create a second user account and change the default ports.
Running as root
The script will not run as root and will error if you try. This is for security and to stop permissions issues. For example, if you run update as root any changed files are then owned by root. This means the csgoserver user will be unable to access the updated files causing the server to fail.
Useful Resources
Here are some useful resources that will help with management and configuration of your server.
Server wiki article: https://developer.valvesoftware.com/wiki/Counter-Strike:_Global_Offensive_Dedicated_Servers
CLI options wiki article: https://developer.valvesoftware.com/wiki/Command_Line_Options
SteamCMD wiki article: https://developer.valvesoftware.com/wiki/SteamCMD
Issues and troubleshooting
If you find a bug or have a suggestion please submit a bug report on GitHub .
https://github.com/dgibbs64/linuxgameservers/issues
If you have a question about the server that is not related to the script please check the games official website.
http://steampowered.com
If you are having issues getting the script to work you probably haven’t followed the instructions correctly. If you are sure you have then please leave a comment below.
GitHub
This script is developed using GitHub you can view the full project here:
https://github.com/dgibbs64/linuxgameservers
Further notes
This script is free to use and you are welcome to customise and change it. I hope the script makes it easier to manage a Counter Strike: Global Offensive server.
Donate
Found my work helpful? Show your appreciation. Please consider donating and help cover my server costs.
PayPal: me@danielgibbs.co.uk
Spread the Word
You can help by spreading the word by letting people know about this script.
Tell your friends, Tweet, Facebook, post on forums or write a blog post.
Also I am interested to know if you are using using this script tweet me.
@dangibbsuk
